Context:
- A report from the US-based cybersecurity firm Resecurity reveals that the personal data of 815 million Indians is currently being sold on the dark web.
Recent Reports on Aadhaar Data Breach
- According to the Resecurity website, an individual using the alias “pwn0001” shared a post on BreachForums (a darknet crime forum) offering access to 815 million records containing information on “Indian Citizen Aadhar and Passport”.
- Resecurity’s investigators found that this threat actor was willing to sell the entire Aadhaar and Indian passport database on hand for $80,000.
What is Aadhar?
- Aadhar number is a 12-digit random number issued by the Unique Identification Authority of India (UIDAI) to the residents of India after satisfying the verification process laid down by the Authority. Any individual, irrespective of age and gender, who is a resident of India, may voluntarily enroll to obtain an Aadhar number.
- The Aadhar number is unique for each individual and will remain valid for life time.
- Virtual ID:VID is a temporary, revocable 16-digit random number mapped with the Aadhar number. VID can be used in lieu of Aadhar number whenever authentication or e-KYC services are performed.
Unique Identification Authority of India (UIDAI)
- The UIDAI is a statutory authority established in 2016.
- Nodal Ministry: Ministry of Electronics and Information Technology,
- Mandate: To assign a 12-digit unique identification (UID) number (Aadhar) to all the residents of India.
|
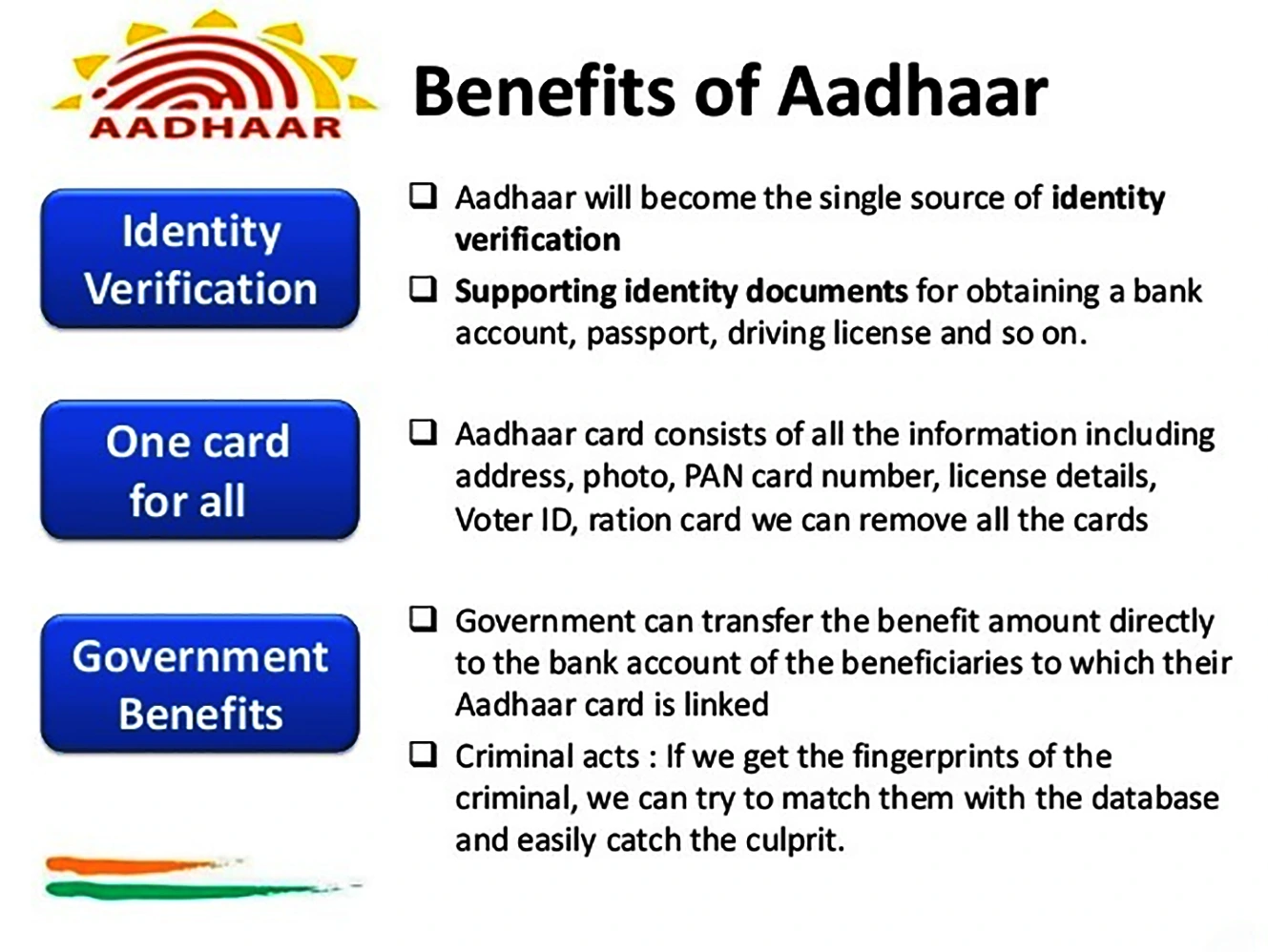
What are the utilities of Aadhar?
- Promoting Good Governance: It is unique and robust enough to eliminate duplicates and fake identities to roll out several Government welfare schemes for effective service delivery thereby promoting transparency and good governance.
- As of July 31, 2023, 765.30 million Indians had linked Aadhar with ration card to avail ration through Public Distribution System. Over 280 million residents linked Aadhar with cooking gas connection for LPG subsidy through PAHAL.
- Boost to Financial inclusion: Aadhar can be used as a permanent Financial Address and facilitates financial inclusion of the underprivileged and weaker sections of the society and is therefore a tool of distributive justice and equality.
- For Example: Jan Dhan Account- Aadhaar- Mobile” (JAM) trinity made it easier for the poor to receive Direct Benefit Transfers (DBTs) of welfare subsidies into their bank account.
- Key Pillar of ‘Digital India’: The Aadhar identity platform is one of the key pillars of the ‘Digital India’, wherein every resident of the country is provided with a unique identity.
- Electronic benefit transfers: The UID-enabled-Bank-Account network will offer a secure and low cost platform to directly remit benefits to residents without the heavy costs associated with benefit distribution; the leakages in the current system will also be stemmed as a result.
- Self-service puts residents in control: Using Aadhar as an authentication mechanism, residents should be able to access up-to-date information about their entitlements, demand services and redress their grievances directly from their mobile phone, kiosks or other means.
- Portability: Aadhaar is a universal number, and agencies and services can contact the central Unique Identification database from anywhere in the country to authenticate a beneficiary’s identity by availing authentication services.
What concerns are associated with the Aadhaar data breach?
- Right to Privacy: As the Supreme Court held that Aadhar could be used for welfare, it recognised a fundamental right to privacy (K.S. Puttaswamy and Anr. vs. Union of India) and struck down Section 57 of the Aadhaar Act which specifically enabled private entities to use Aadhaar numbers to establish identity for delivering services.
- Data Breaches: Many private entities in the country insist on an Aadhar card, and users often share the details. There’s no clarity on how these entities keep these data private and secure.
- For Example: While data breaches in Aadhaar have been reported in 2018, 2019, and 2022.
- Security concerns: Several studies and news reports have highlighted how using AePS, money from workers’ accounts have been withdrawn or that they have been signed up for government insurance programmes without their knowledge.
- The ₹10 crore scholarship scam in Jharkhand from 2020 exemplifies this.
- Excessive Aadhaar imposition:In its September 2018 judgment, the Supreme Court ruled that Aadhaar authentication can be made mandatory only for benefits paid from the Consolidated Fund of India and that alternative means of identity verification must always be provided when Aadhaar fails.
- Instead, Aadhaar continues to be routinely demanded from children for basic rights such as anganwadi services or school enrolment.
- Unreliable demographic details: The demographic details on an Aadhaar card are often unverified and unreliable, particularly the person’s age (date of birth). Yet, Aadhar-based age is frequently used to check eligibility for old-age pensions or school admission, and even to assign children to a particular grade.
- Challenges in Aadhaar Authentication Process in Rural Areas: In many rural areas, people have to make multiple trips to ration shops, to authenticate with no guarantee that the authentication will work.
- Lack of reliable internet, fading fingerprints among daily wage workers, lack of phone connectivity to get an OTP etc. lead to denials of benefits of welfare schemes.
Aadhaar-enabled Payment Services (AePS)
- AePS is a bank-led model which allows online financial transactions at Point-of-Sale (PoS) and Micro ATMs through the business correspondent of any bank using Aadhaar authentication.
|
What measures has UIDAI implemented to secure Aadhaar data?
- Central Identities Data Repository (CIDR): Data of all Aadhaar holders is safe and secure in the Central Identities Data Repository (CIDR) of UIDAI.
- Collaborative Approach: UIDAI works closely with all user agencies to enhance data security measures when it comes to sensitive user details like Aadhar.
- Advanced security technologies: UIDAI uses advanced security technologies to keep data safe and keeps upgrading them to meet emerging security threats and challenges.
Also Read: Digital Personal DataProtection Bill 2023
Way Forward
- Masked Aadhaar: The UIDAI, recommended that “a masked Aadhaar, which displays only the last four digits of your Aadhaar number,” should be used.
- Reinstating Independent Oversight in the Aadhaar Act for Accountability: The draft of the Aadhaar Act included an entire chapter aimed at ensuring independent oversight of the Unique Identification Authority of India by a high-powered “Identity Review Committee”.
- This chapter, however, was dropped in the final version of the Aadhaar Act. Ideally, the Act should be amended to reinstate provisions for independent oversight of the Unique Identification Authority of India.
- Alternative to Aadhaar authentication: The government must abide by and enforce Supreme Court directions, including- restriction of mandatory Aadhar to permissible purposes, provision of an alternative whenever Aadhar authentication fails.
- Locking Aadhaar Information: Users should lock their Aadhaar information by visiting the UIDAI website or using the mobile app to ensure that their biometric information, even if compromised, cannot be used to initiate financial transactions.
- Multipronged Approach: Adopting measures like encryption, multifactor authentication and access controls are vital to protect data. Regular security audits and updates are also components of a cybersecurity strategy that can adapt to emerging threats effectively.
Conclusion:
The Aadhaar data breach highlights the importance of better security, oversight, and protective measures to safeguard personal information and ensure privacy rights.
| Prelims Question (2018)
Right to Privacy is protected as an intrinsic part of Right to Life and Personal Liberty.
Which of the following in the Constitution of India correctly and appropriately imply the above statement?
(a) Article 14 and the provisions under the 42nd Amendment to the Constitution
(b) Article 17 and the Directive Principles of State Policy in Part IV
(c) Article 21 and the freedoms guaranteed in Part III
(d) Article 24 and the provisions under the 44th Amendment to the Constitution
Ans: (c) |
![]() 31 Oct 2023
31 Oct 2023

