India’s first joint doctrine for cyberspace operations was released by the Chief of Defence Staff General Anil Chauhan at a meeting of the Chiefs of Staff Committee.
Global Commons
- Global Commons are defined as natural assets which are outside national jurisdictions.
- They are resource domains to which all nations have legal access and are not under the control of a particular state but are open for use by all countries, organizations, and individuals.
- Examples: High Seas, atmosphere, outer space and the Antarctic.
- Shared sovereignty: A global common is not an absence of sovereignty but rather shared global sovereignty.
- Reason for exceptions to the state sovereignty principle:
- Ungovernable domains : Countries lack the capacity to realistically govern and exercise control over these inaccessible or otherwise ubiquitous domains all by themselves.
- International Conflict: Multiple claims over such domains have the potential to spark off international conflict
- Mutual interest: Countries will be mutually benefited in free use and access of these domains.
|
Key Highlights On India’s First Joint Doctrine for Cyberspace Operations
- A guiding tool: It is a keystone publication that will guide commanders of the armed forces in conducting cyberspace operations in today’s complex military operating environment.
- The Doctrine emphasizes on: Importance will be placed on understanding military aspects of cyberspace operations and providing conceptual guidance for planning, and conduct of operations in cyberspace, as also to raise awareness in our warfighters at all levels.
Enroll now for UPSC Online Course
Why is a Joint Doctrine for Cyberspace Doctrine Needed?
- Integration between the forces: The Joint Doctrine will enable Jointness and Integration amongst the forces for Cyberspace Operations.
- Integrated into national security fabric: Operations in cyberspace need to be integrated into the national security fabric, to evolve the ‘ends,’ ‘ways’ and ‘means’ to create advantage and influence events in all other operational environments and across all instruments of power
- Shared sovereignty: Cyberspace is a global common and hence has shared sovereignty, therefore a common, collaborative and integrated doctrine is needed to deal with the risk of cyberspace warfare.
- Widespread impacts: Hostile actions in cyberspace can impact the nation’s economy, cohesion, political decision making, and the ability to defend itself.
Cyberspace Warfare
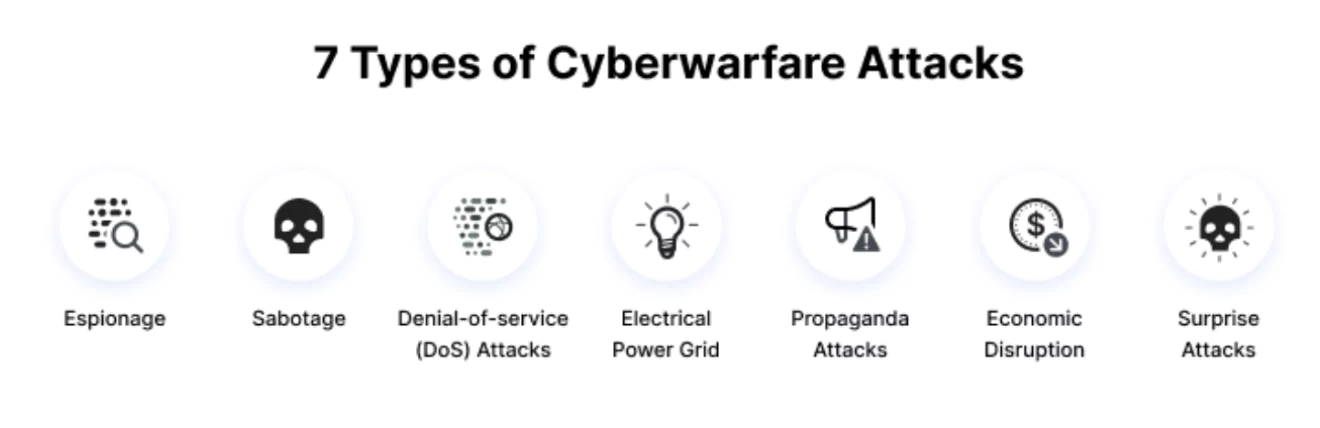
- About: Cyber warfare involves the hostile actions by a nation-state or international organization or Non-state actors with the intention of disrupting, damaging, or destroying another nation’s computers or information networks infrastructure through, for example, computer viruses or denial-of-service attacks.
|
Motivations for Cyber Warfare
- Military: An effective cyberattack could bring an enemy country’s military to its knees by incapacitating its weaponry systems and hacking its communication network, securing an easy victory.
- Example: A copy of Remote Manipulator System (RMS), a utilities software tool that enables remote control of devices, was being distributed in Ukraine via fake “Evacuation Plan” emails.
- Civil: Attacking the civil infrastructure of a nation directly impacts the people of the country causing widespread political instability by instilling fear and distrust for the leadership causing them to revolt against the government.
- Example: In March 2014, Russia levied a distributed denial-of-service (DDoS) attack on Ukraine and also crippled Ukraine’s election commission.
- Hacktivism: Hacktivism involves hackers using cyberattacks to promote an ideology. Hacktivists can engage in cyber warfare by spreading propaganda and weakening an opponent’s standing on the world stage, precluding support from other countries.
- Example: An attack on Sony Pictures followed the release of the film “The Interview”, which presented a negative portrayal of Kim Jong Un.
- Income generation: Cyber warfare “soldiers” can engage in such attacks for monetary benefits whether employed by the government, or for their own ulterior motives.
- Example: In 2015, Chinese hackers stole millions of records from the United States’ Office of Personnel Management (OPM)
- Nonprofit research: Nonprofit research often reveals very valuable information that a country can use to solve a critical problem. For example: if a country is trying to develop a vaccine and another one already has it, cyber warfare could be used to steal information pertaining to their solution.
Response to Cyber Warfare
- Conducting Risk Assessments with Cyber Wargames: A real life wargame can test the response to a cyber warfare scenario, expose gaps in defenses, and improve cooperation between entities. It will be a learning tool for the defenderson how to act quickly to protect critical infrastructure and save lives
- Layered Defense Approach: A layered defense approach includes,
- Securing the cyber ecosystem
- Raising awareness for cybersecurity
- Promoting open standards for combating cyber threats
- Implementing a national cybersecurity assurance framework
- Working with private organizations to improve their cybersecurity capabilities
- Securing Private sector: Businesses need a set of measures to ensure corporate cybersecurity, which can also promote national security by,
- Create obstacles to breaching the network
- Use web application firewalls (WAF) to quickly detect, investigate, and block malicious traffic
- Quickly respond to a breach and restore business operations
- Facilitate cooperation between the public and private sectors
- Use local hackers as a resource to help protect against foreign cyber threats.
Check Out UPSC CSE Books From PW Store
India’s Government Initiatives for Cybersecurity
- The Indian Computer Emergency Response Team (CERT-In): The CERT-In plays the central role for incident response, vulnerability handling, and security management in India’s cyberspace
- Cyber Surakshit Bharat: It was launched by the Ministry of Electronics and Information Technology (MeitY) with National Electronic Governance Division (NeGD) to ensure more awareness about the latest cybercrimes and the cybersecurity challenges of India.
- Cyber Swachhta Kendra: The initiative focuses on detecting and removing malicious botnet programs from computers and devices. It provides free tools for malware analysis and helps improve the security of systems and devices.
- National Cybersecurity Policy 2020: It provides a framework for creating a secure cyber ecosystem and aims to protect information and other critical infrastructure.
- The National Critical Information Infrastructure Protection Centre (NCIIPC): It was established for the protection of critical information infrastructure in the country.
- Indian Cyber Crime Coordination Centre (I4C): It focuses on tackling all the issues related to Cybercrime for the citizens, which includes improving coordination between various Law Enforcement Agencies and the stakeholders, and to improve citizen satisfaction levels.
|
![]() 19 Jun 2024
19 Jun 2024
