Dodol
|
- Recently the Goa government formally applied for a Geographical Indication (GI) tag for the Goan sweet called Dodol.
Dodol:
- About: Dodol is a classic Goan sweet that is often called a cousin of Bebinca, the ‘Queen of Goan desserts’.
- History: In Goa, it is believed that the sweet was introduced during Portuguese rule in the coastal state during the 17th century.
- Some scholars claim a traditional version of the sweet was served in the royal banquets in the Medang Kingdom of Indonesia between the 8th and 11th centuries.
- Variations: Dodol and its variations are also popular in southern India, Sri Lanka, Indonesia, Thailand, Malaysia, and parts of Southeast Asia.
Geographical Indication Tag:
- About: A Geographical Indication (GI) tag certifies unique products based on their origin and is defined by Articles 23 and 24 of the Trade-Related Aspects of Intellectual Property Rights (TRIPS) Agreement of the World Trade Organization (WTO).
- Rule: Products with a GI tag can be natural or man-made. The raw materials used for these products do not necessarily need to originate from the specific geographical region, except in the case of agricultural tags.
- Collective Intellectual Property: The fundamental distinction between GI and other intellectual properties (IP) lies in GI being a collective Intellectual Property Right.
- India: India, a WTO member, implemented the Geographical Indications of Goods (Registration & Protection) Act in 1999, which became effective in 2003.
|
Chat Control Law
|
- Recently, the European Union proposed Chat Control legislation, intended to address online child sexual abuse, has ignited vigorous debate among member states regarding privacy concerns and the risk of misuse.
Chat Control Law:
- About: The legislation includes clauses for conducting widespread scanning of private messages and circumventing end-to-end encryption.
- Critics contend that these scanning practices introduce security vulnerabilities, creating potential backdoors that could be exploited by malicious third parties.
- Potential Misuse : Critics also highlight concerns that authoritarian regimes could exploit the scanning technology to target dissidents.
- The revised draft restricts scanning to images, videos, and URLs, omitting text and audio messages.
- Consent Requirement: Another modification mandates user consent for scanning. However, refusal would result in blocking multimedia sharing, rendering the “choice” effectively meaningless.
End-to-End Encryption (E2E Encryption)
- About: End-to-end encryption (E2E encryption) is a technique where data is encrypted from its origin to its destination, ensuring continuous protection throughout its journey.
- Encryption-in-Transit: Encryption-in-transit safeguards data while it travels between your device and the server.
- Comprehensive Data Protection: E2E encryption secures data during both transmission and storage on servers, decrypting it only when received by the intended recipient.
|
Niger’s China-backed oil pipeline
|
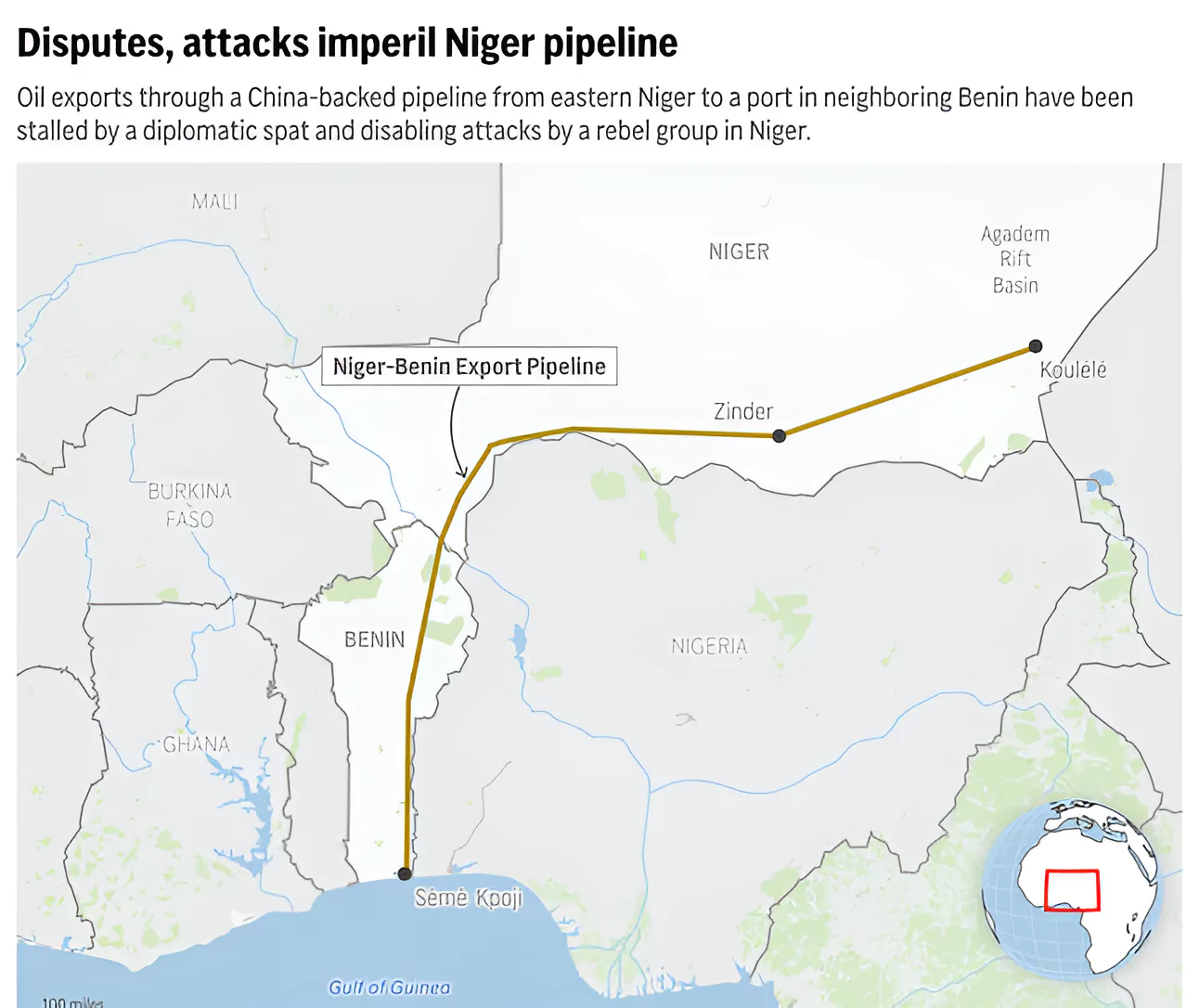
- A China-backed pipeline that would make Niger an oil-exporting country is being threatened by an internal security crisis and a diplomatic dispute with neighbouring Benin
Pipeline:
- About: The 1,930-kilometre (1,200-mile) pipeline runs from Niger’s Chinese-built Agadem oil field to the port of Cotonou in Benin.
- Objective: To help the oil-rich but landlocked Niger achieve an almost fivefold increase in oil production through a $400 million deal signed in April with China’s state-run national petroleum company.
|
Space Variable Objects Monitor (SVOM) satellite
|
- Recently, a Long March 2-C rocket launched the French-Chinese satellite Space Variable Objects Monitor (SVOM) successfully from southwestern China.
Space Variable Objects Monitor (SVOM) Satellite:
- About: The SVOM satellite, a joint French-Chinese mission designed to detect and study gamma-ray bursts, was launched from the Xichang Satellite Launch Center in southwest China’s Sichuan Province using a Long March-2C rocket.
- Lifespan: The satellite has been placed into an orbit more than 600 kilometres above Earth with a planned operational lifespan of five years. However, scientists anticipate it could remain functional for up to 20 years.
Gamma-ray bursts (GRBs):
- Origins: Gamma-ray bursts (GRBs) typically occur following the explosion of massive stars, which are more than 20 times the size of the sun, or from the merger of compact stars.
- These immensely bright cosmic phenomena can emit energy bursts equivalent to over a billion billion suns.
- Traces of Cosmic Journey: Gamma-ray bursts (GRBs) carry imprints of the gas clouds and galaxies they traverse in space, providing valuable data for comprehending the universe’s history and evolution.
- Challenges of GRB Observation: Gamma-ray bursts (GRBs) are exceptionally difficult to detect due to their unpredictable appearance across the sky and brief durations lasting only a few seconds.
- These bursts are largely absorbed by Earth’s atmosphere, necessitating space probes for observation and recording.
|
Zero knowledge proof
|
- About: A cryptographic method, zero knowledge proof is a way by which a party (called the prover) convinces the other party (called the verifier) that it possesses a piece of data or information, without revealing the data itself.
- While zero proof knowledge techniques have been around for decades now, there has been renewed interest with the advent of blockchain technology.
|
Sovereign cloud
|
- About: A sovereign cloud is a cloud computing environment that addresses data residency, security and compliance concerns specifically for a country or jurisdiction.
- Difference: Unlike traditional services provided by tech giants, sovereign cloud solutions are hosted and managed within the geographical boundaries of the country they serve.
- Governments and institutions handling sensitive information like citizen data, intellectual property or classified information prefer sovereign cloud.
|
Deadpool
|
- About: In the context of startups, deadpool refers to a list of companies that have shuttered and ceased operations.
- Deadpool sometimes may also include companies that have been acquired or have completely pivoted. It is can be a useful for investors and entrepreneurs to gain insights on specific industries, and mitigate potential risks in their own ventures.
|
![]() 24 Jun 2024
24 Jun 2024