![]() June 7, 2024
June 7, 2024
![]() 1651
1651
![]() 0
0
Cryptography is a cornerstone of modern Information and Communication Technology (ICT), serving as a robust mechanism to secure information and communications. By transforming data into unreadable formats, it ensures confidentiality, integrity, and authenticity. This digital safeguard is indispensable for protecting sensitive information in various applications, from secure communications to identity management.
An Overview Of Cryptography
About: It plays a vital role in securing information and communication within the vast realm of Information and Communication Technology (ICT).
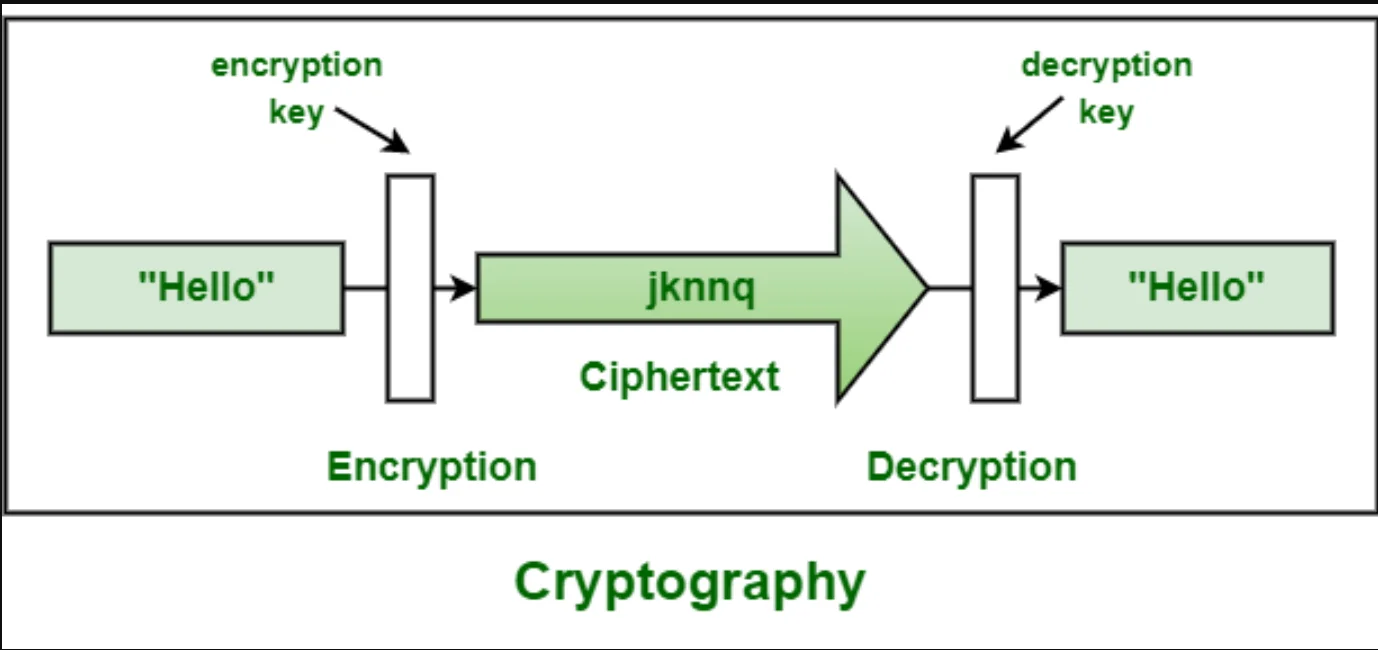
About: It is a secure way to electronically sign documents and other digital files.
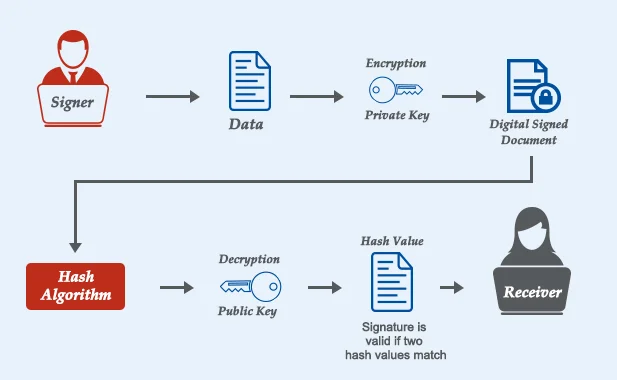
| Digital Signature Certificates (DSCs) and their Legality in India
In India, digital signature certificates (DSCs) are legally valid and recognized as equivalent to handwritten signatures under the Information Technology Act, 2000 (IT Act, 2000). |
| Must Read | |
| Current Affairs | Editorial Analysis |
| Upsc Notes | Upsc Blogs |
| NCERT Notes | Free Main Answer Writing |
Conclusion
Cryptography is integral to maintaining security and trust in the digital world. By protecting data in transit and at rest, and enabling secure authentication and authorization, it fortifies the ICT infrastructure. As digital interactions continue to expand, the role of cryptography in ensuring secure and reliable communication becomes increasingly crucial.
<div class="new-fform">
</div>
Latest Comments