The Ear, Nose & Throat (ENT) department at Command Hospital in Pune conducted two piezoelectric Bone Conduction Hearing Implants (BCI).
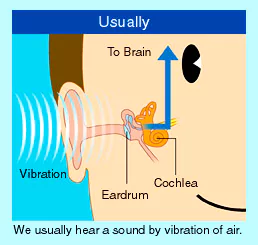
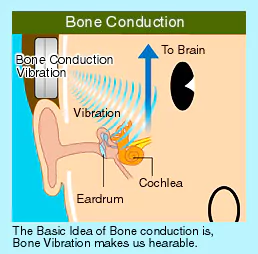
What is the Piezoelectricity?
|
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
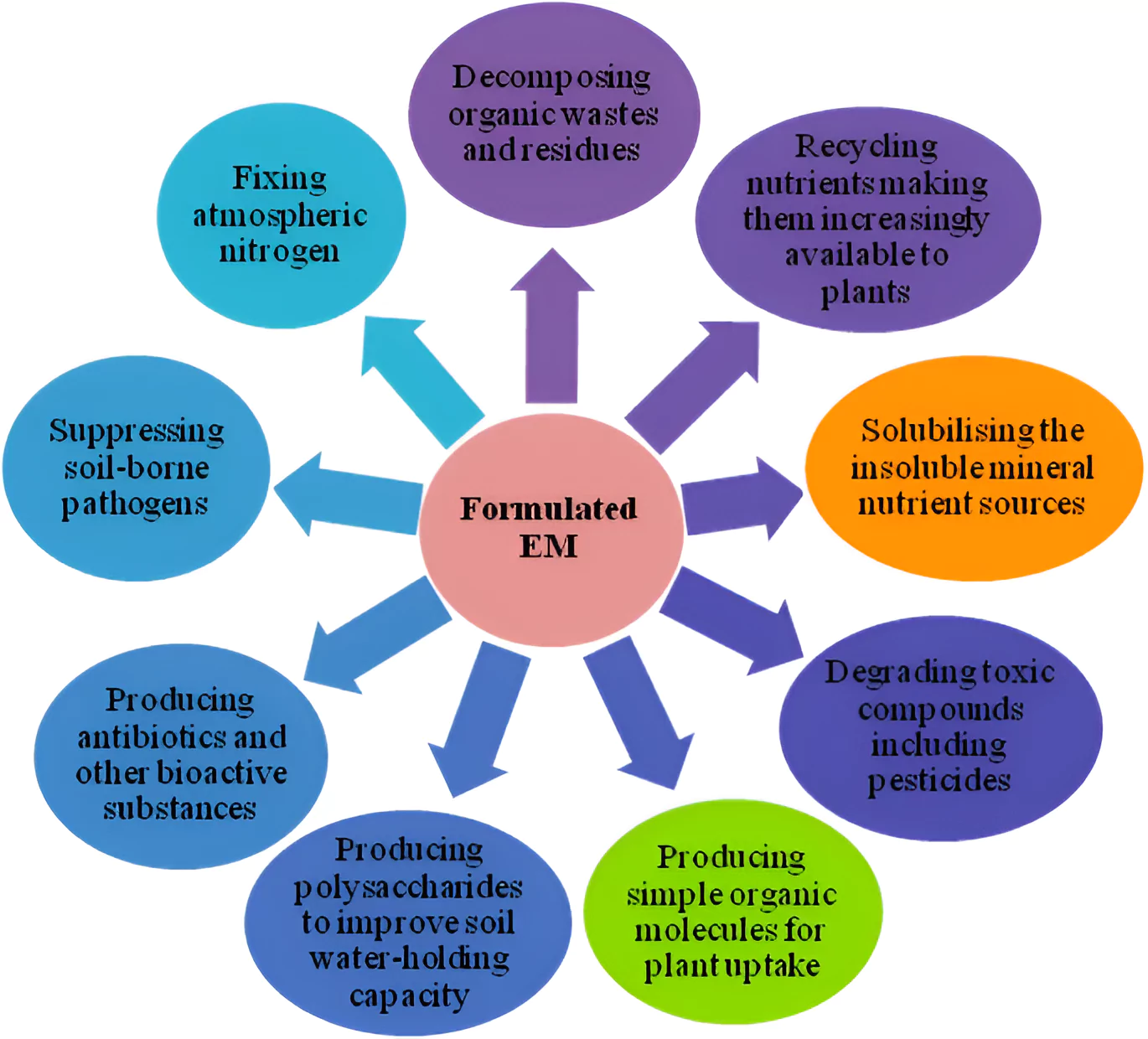
Three new microbial formulations based on granular lime and gypsum have been developed and validated by The ICAR- Indian Institute of Spices Research (IISR), Kozhikode.
Microbial Formulation
|
|---|
Use of Gypsum (Calcium sulphate dihydrate) in Agriculture
|
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Recently, the Supreme Court ruled that election candidates have a right to privacy and are not required to disclose every detail of their personal life and belongings to voters.
(RPA) Representation of the People Act 1951
|
|---|
Right to Privacy
|
|---|
Previous Legal Case Overview
|
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Recently, The 2024 Plastic Overshoot Day Report was released by Swiss-based research consultancy ‘Earth Action (EA)’.
Finding Related to World Wide:
Findings Related to India:
|
|---|
Key Terminology:
|
|---|
To end plastic pollution:
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Recently, For the first time in India, a Eurasian otter was radio-tagged in the Satpura Tiger Reserve (STR) in Narmadapuram district in Madhya Pradesh.
 Habitat: The Eurasian otter lives in a wide variety of aquatic habitats, including highland and lowland lakes, rivers, streams, marshes, swamp forests and coastal areas.
Habitat: The Eurasian otter lives in a wide variety of aquatic habitats, including highland and lowland lakes, rivers, streams, marshes, swamp forests and coastal areas. 
Satpura Tiger Reserve, Madhya Pradesh
|
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Recently, Apple issued alerts to iPhone users in 92 countries including India,cautioning them from mercenary spyware attacks including Pegasus.
National cyber security agency, Computer Emergency Response Team (CERT-In) has issued a warning against Malware Attack in India‘Akira’:
‘Daam’:
Raccoon Stealer Malware:
Hermit Spyware:
|
|---|
Companies producing mercenary spyware include the NSO Group, FinFisher, and Hacking Team.
Communication Surveillance in India:
|
|---|
Types of Malware |
| Ransomware: In a ransomware attack, an adversary encrypts a victim’s data and offers to provide a decryption key in exchange for a payment. |
| Fileless Malware: Fileless malware is a type of malicious activity that uses native, legitimate tools built into a system to execute a cyber attack. |
| Spyware: Spyware is a type of unwanted, malicious software that infects a computer or other device and collects information about a user’s web activity without their knowledge or consent. |
| Adware: Adware is a type of spyware that watches a user’s online activity in order to determine which ads to show them. |
| Trojan: A trojan is malware that appears to be legitimate software disguised as native operating system programs or harmless files like free downloads. |
| Worms: A worm is a self-contained program that replicates itself and spreads its copies to other computers. |
| Rootkits: Rootkit malware is a collection of software designed to give malicious actors control of a computer network or application. |
| Bootkits take this a step further by infecting the master boot prior to the operating system being on boot up, going undetectable at times. |
| Mobile Malware: Mobile malware is any type of malware designed to target mobile devices. Mobile malware is delivered through malicious downloads, operating system vulnerabilities, phishing, smishing, and the use of unsecured WiFi. |
| Exploits: An exploit is a piece of software or data that opportunistically uses a defect in an operating system or an app to provide access to unauthorized actors |
| Scareware: Scareware tricks users into believing their computer is infected with a virus. |
| Keylogger: Keyloggers are tools that record what a person types on a device. In a keylogger attack, the keylogger software records every keystroke on the victim’s device and sends it to the attacker. |
| Botnet: Botnet is a network of computers infected with malware that are controlled by a bot herder. The bot herder is the person who operates the botnet infrastructure and uses the compromised computers to launch attacks designed to crash a target’s network, inject malware, harvest credentials or execute CPU-intensive tasks. |
| MALSPAM: Malicious malware (MALSPAM) delivers malware as the malicious payload via emails containing malicious content, such as virus or malware infected attachments. |
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Recently, The Corporate Climate Responsibility Monitor 2024 report was released by the non-profit New Climate Institute with assistance from Carbon Market Watch.
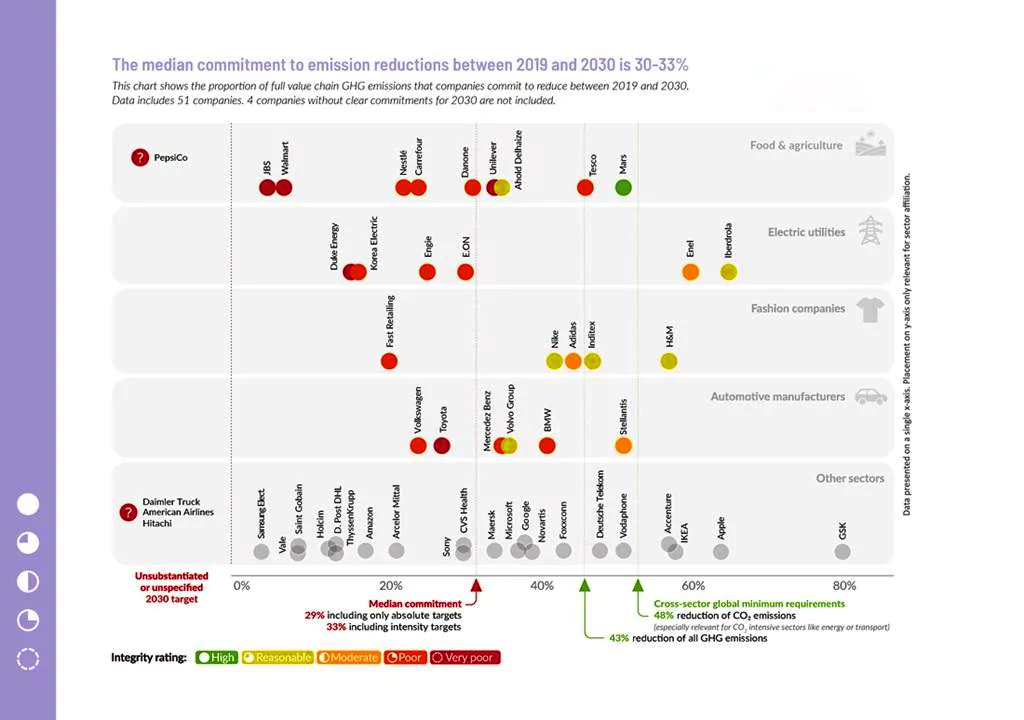
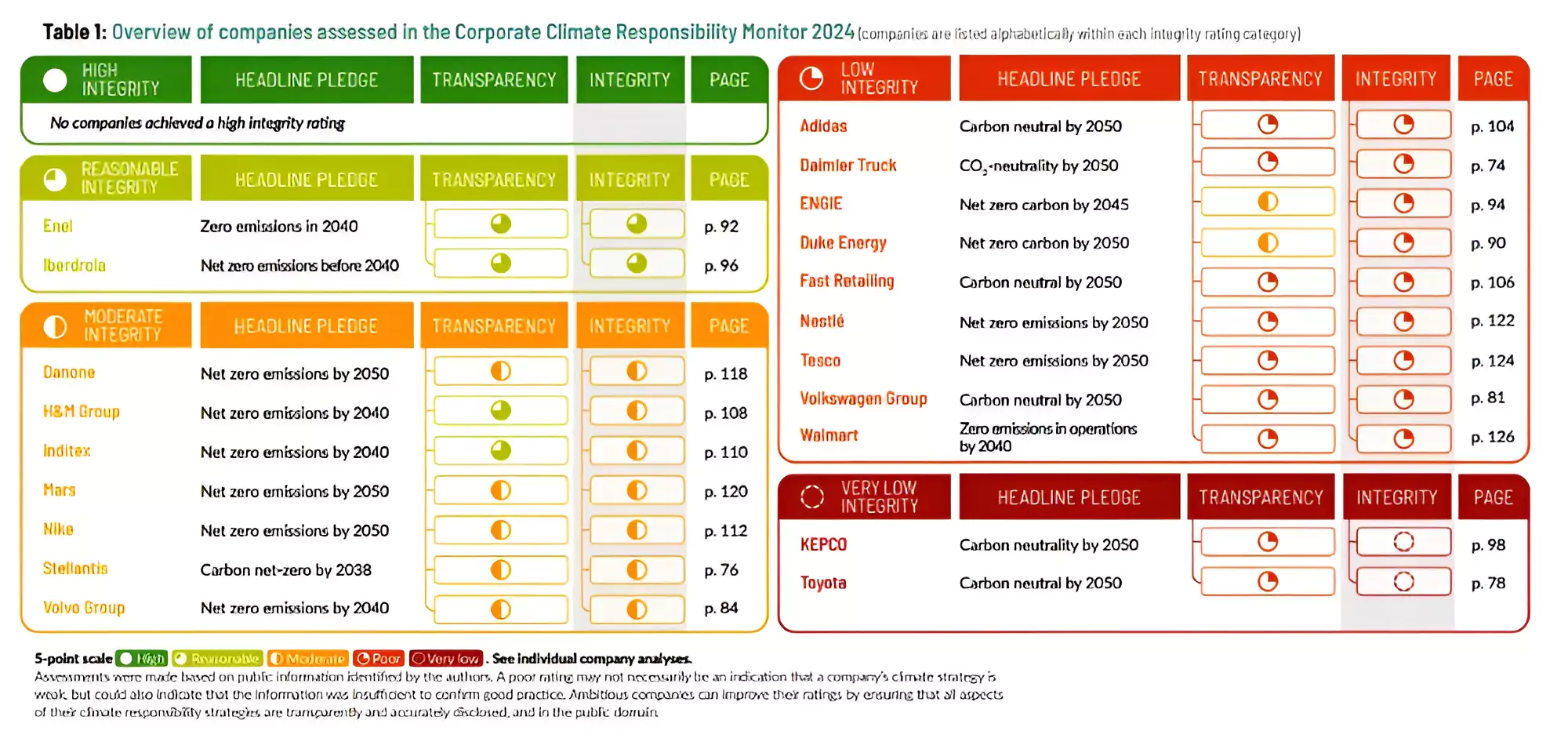
Carbon offsetting
|
|---|
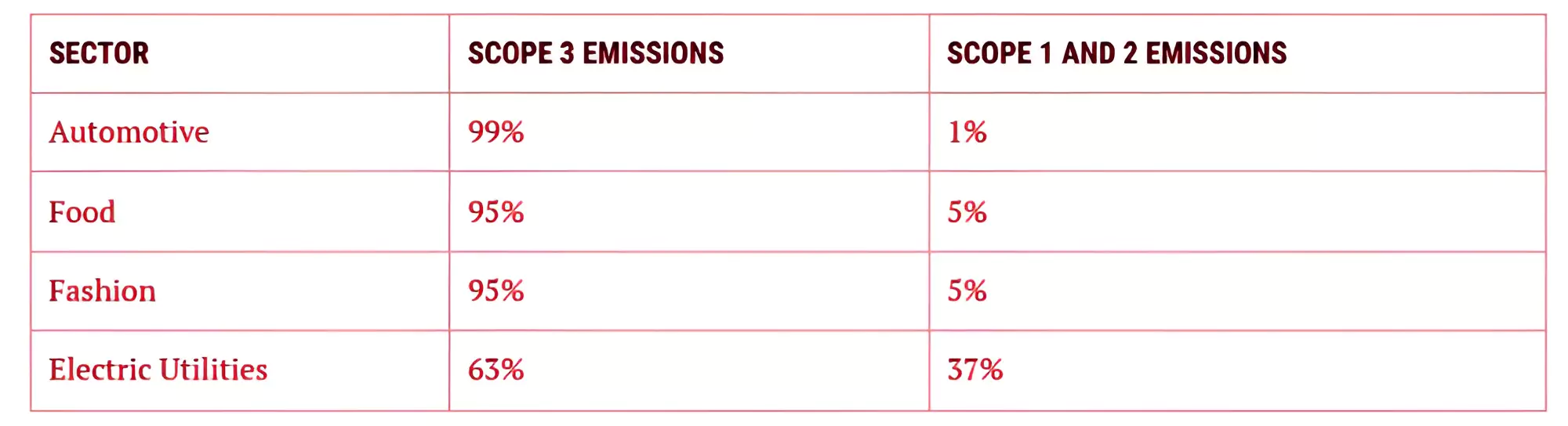 Scope 2 Emissions: This relates to a company’s energy usage, such as the electricity it consumes.
Scope 2 Emissions: This relates to a company’s energy usage, such as the electricity it consumes.Impact of Flexible Offsetting
|
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
Telecom Regulatory Authority of India (TRAI) has released its recommendations on Encouraging Innovative Technologies, Services, Use Cases, and Business Models through Regulatory Sandbox in Digital Communication Sector.
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
The President of India, Smt. Droupadi Murmu extended warm wishes on the eve of Vaisakhi, Vishu, Bishub, Bahag Bihu, Poila Boishakh, Vaishakhadi and Puthandu.

Here is a list of traditional “New Year Festivals in India”;
 Traditional Customs: During Vaishakhadi, people visit gurdwaras, participate in processions called Nagar Kirtan, and indulge in traditional Punjabi music and dance like Bhangra and Gidda.
Traditional Customs: During Vaishakhadi, people visit gurdwaras, participate in processions called Nagar Kirtan, and indulge in traditional Punjabi music and dance like Bhangra and Gidda.

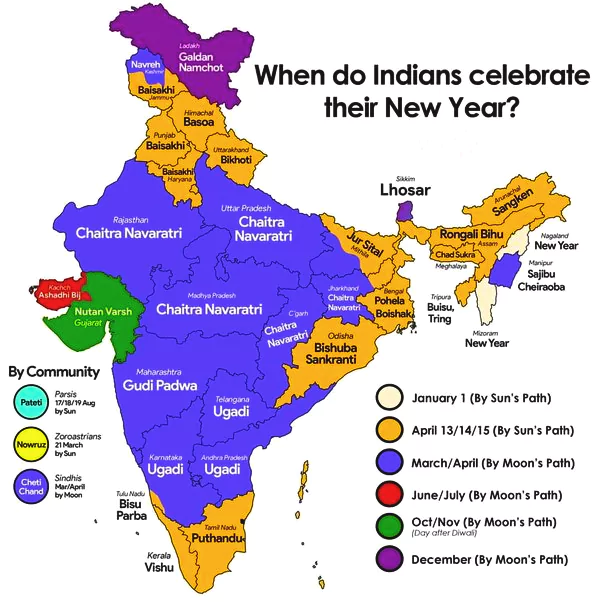 Celebrations: Bihu dance performances, feasting, and community gatherings are common.
Celebrations: Bihu dance performances, feasting, and community gatherings are common.  Gudi Dvaja: This special setup includes a cloth, often a saree or dhoti, adorned with flowers, mango leaves, and neem leaves.
Gudi Dvaja: This special setup includes a cloth, often a saree or dhoti, adorned with flowers, mango leaves, and neem leaves.
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
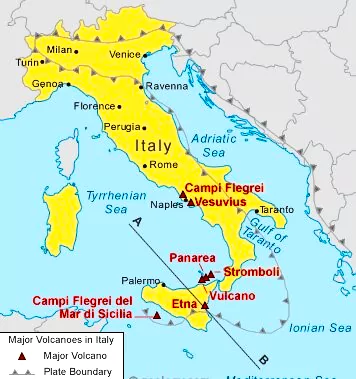
Mount Etna Smoke: Mount Etna, the largest volcano in Europe, has been sending up almost perfect rings of smoke into the air.
| Relevance For Prelims: Volcanic Vortex Rings, Mount Etna, Exploring Volcanoes, Volcanic Landforms, Distribution Of Volcanoes, Largest Volcanoes In The World List, Volcano Eruption In Iceland, and Indonesia Merapi Volcano Eruption.
Relevance For Mains: Volcanoes: Types, Geographical Distribution, Positive and Negative Impacts. |
|---|
|
|---|
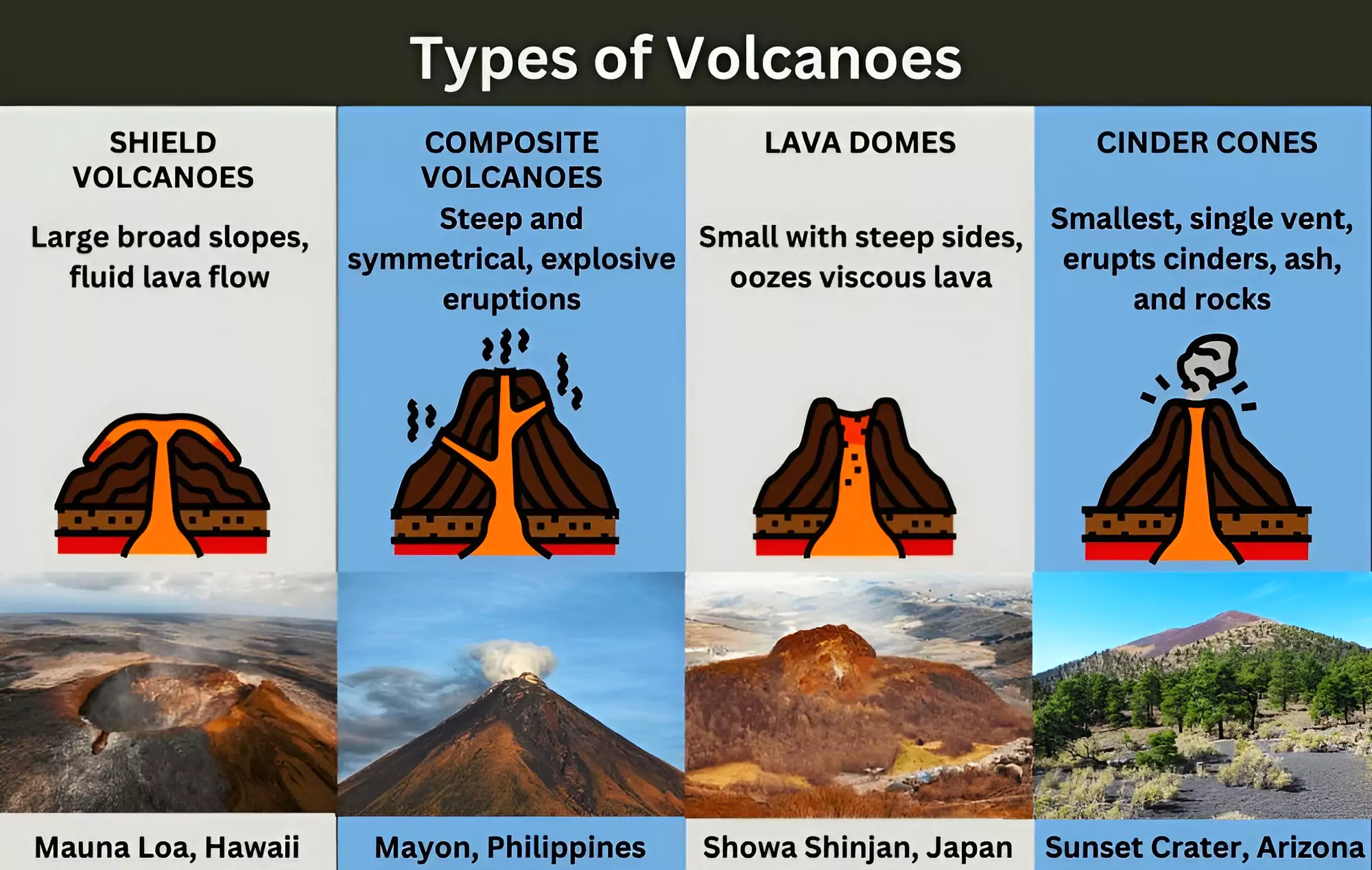
There are about 500 volcanoes in the world. Most of these volcanoes are found in
three well defined belts.

Positive consequences of volcanic eruptions are;
Negative consequences of volcanic eruptions are;
| Prelims PYQ (2014):
Which of the following adds/ads carbon dioxide to the carbon cycle on the planet Earth? 1. Volcanic action 2. Respiration 3. Photosynthesis 4. Decay of organic matter Select the correct answer using the code given below. (a) 1 and 3 only (b) 2 only (c) 1, 2 and 4 only (d) 1, 2, 3 and 4 Ans: (c) |
|---|
| Mains Question: Define volcanic hotspots and expound upon their key characteristics. (10 M, 150 Words) |
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
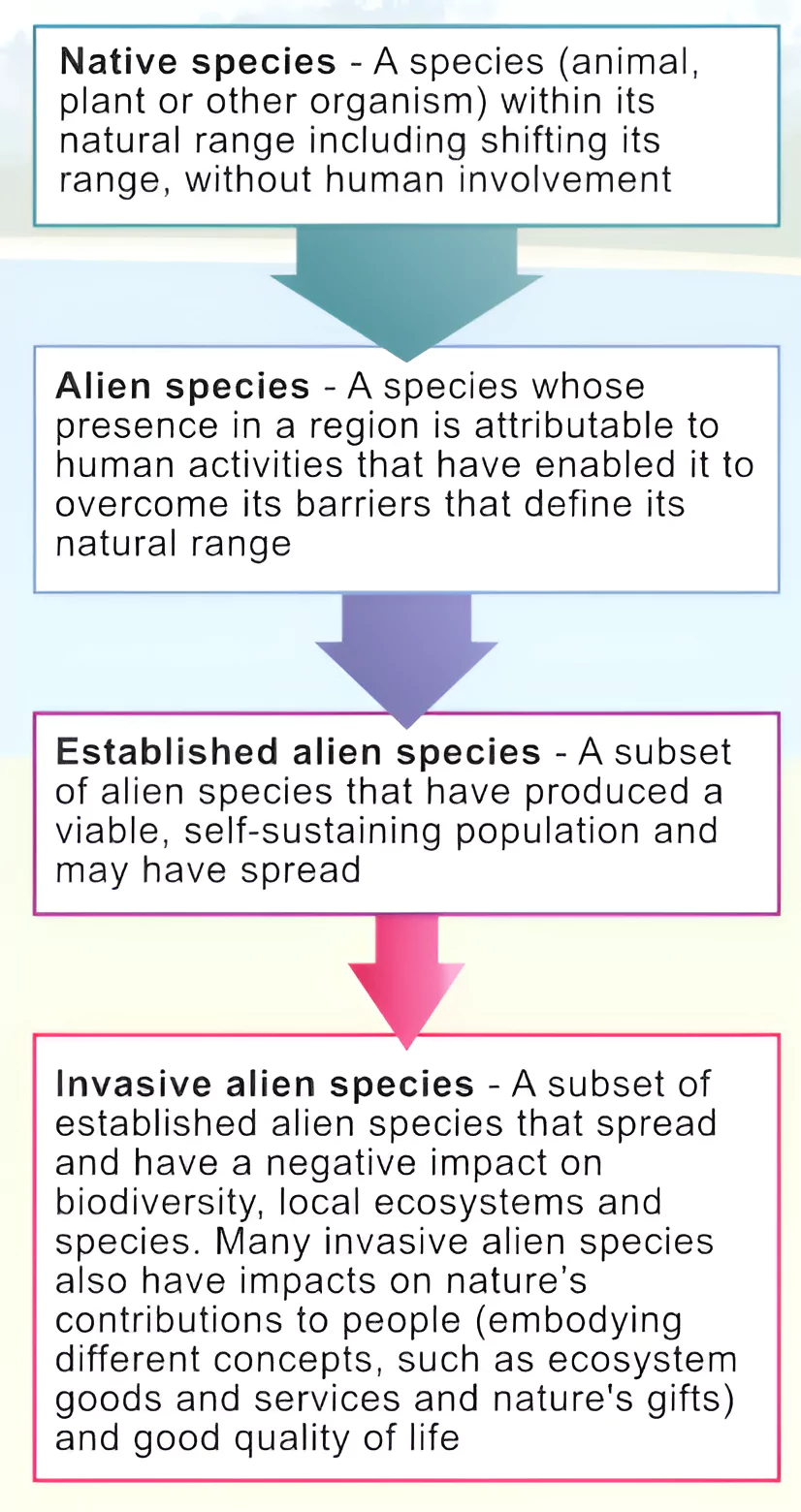
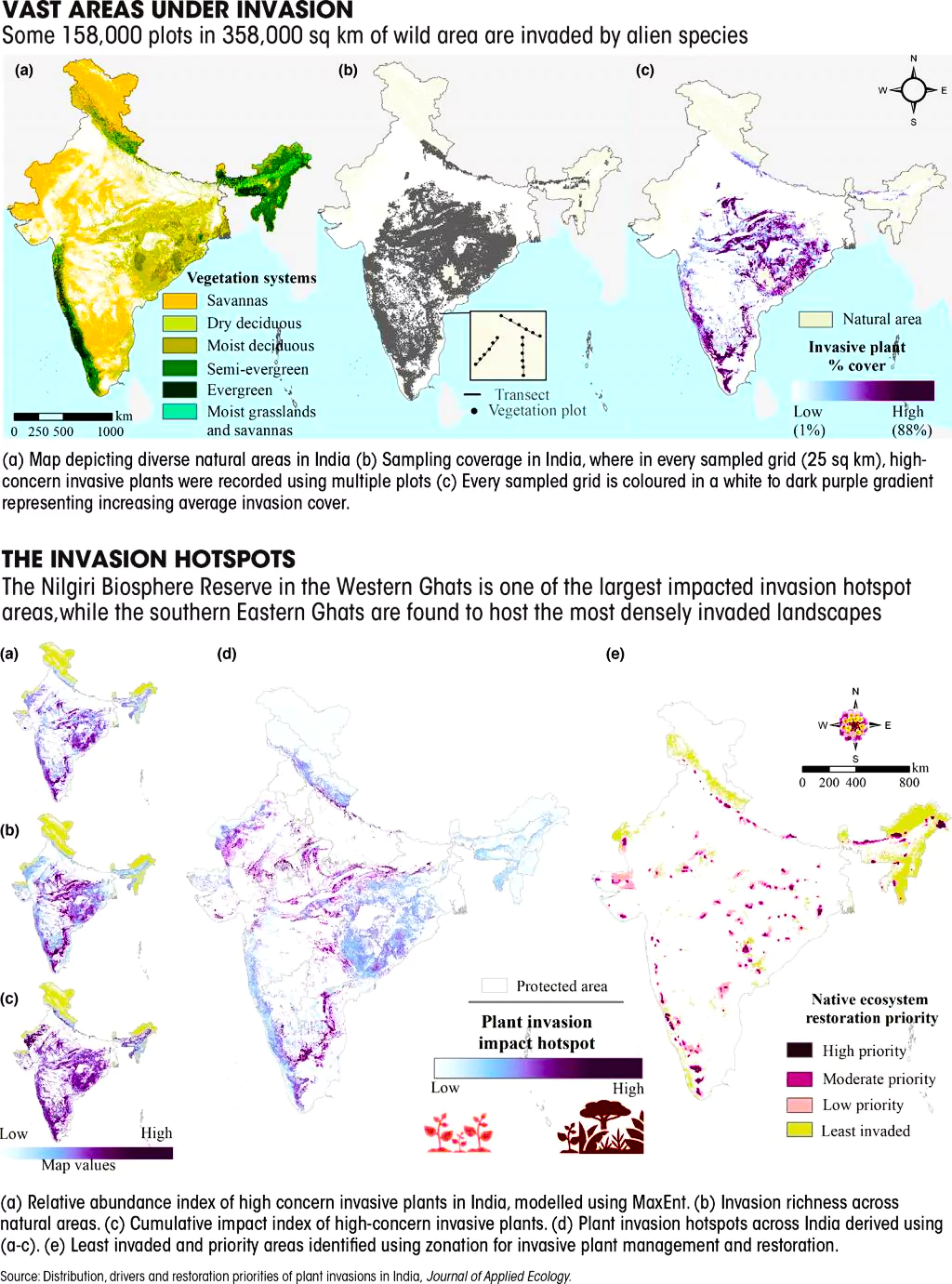
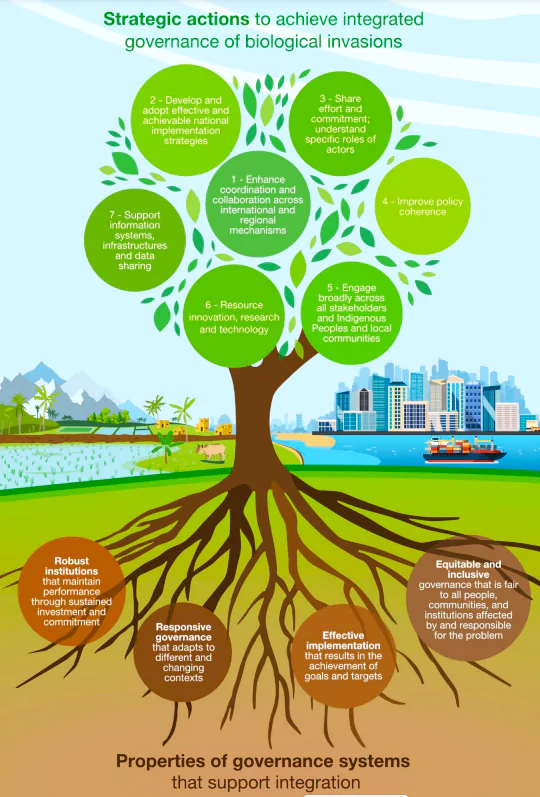
The Andaman and Nicobar Islands administration recently sought help from the Wildlife Institute of India to manage the teeming population of chital (spotted deer) in Ross Island (officially known as the Netaji Subhash Chandra Bose Island).
| Relevance For Prelims: Andaman and Nicobar Islands (ANI), Chital (Spotted Deer), Rise Of Invasive Species In India, BIODIVERSITY, Forest Fires In India, and United Nations Convention On Biological Diversity (UNCBD).
Relevance For Mains: Invasive Alien Species in India: Challenges, and Way Forward. |
|---|
About Chital (Spotted Deer or Axis Deer)Chital, native to mainland India, were introduced to the tiny island by the British in the early 20th century. Having no natural predators or competitors, and being good swimmers, chital swiftly spread across the Andamans.
|
|---|
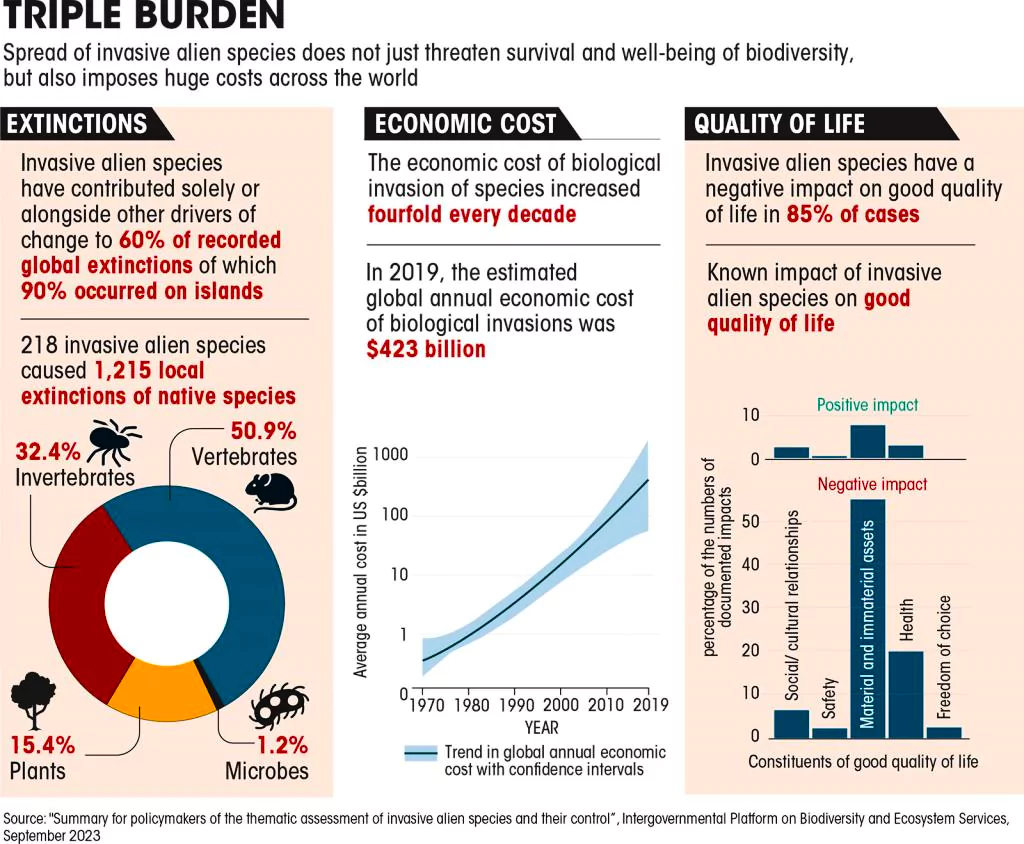 Habitat Degradation: With rising urbanisation, construction projects, deforestation, and unsustainable land-use changes are also increasing and disrupting and degrading the native ecosystems and allowing Invasive Alien Species to establish themselves in those habitats easily.
Habitat Degradation: With rising urbanisation, construction projects, deforestation, and unsustainable land-use changes are also increasing and disrupting and degrading the native ecosystems and allowing Invasive Alien Species to establish themselves in those habitats easily.
| Prelims PYQ (2020):
If a particular plant species is placed under Schedule VI of The Wildlife Protection Act, 1972, what is the implication? (a) a license is required to cultivate that plant. (b) Such a plant cannot be cultivated under any circumstances. (c) It is a Genetically Modified crop plant. (d) Such a plant is invasive and harmful to the ecosystem. Ans: (a) |
|---|
| Must Read | |
| NCERT Notes For UPSC | UPSC Daily Current Affairs |
| UPSC Blogs | UPSC Daily Editorials |
| Daily Current Affairs Quiz | Daily Main Answer Writing |
| UPSC Mains Previous Year Papers | UPSC Test Series 2024 |
<div class="new-fform">
</div>